Let’s be honest—managing local admin accounts on macOS has always been a bit of a mess. From clunky scripts to half-baked MDM workarounds, it’s never felt as clean or secure as it should. But with the latest updates from Microsoft Intune, we finally have something that feels right: macOS LAPS.
🧠 What is LAPS, Anyway?
LAPS (Local Administrator Password Solution) for macOS is Microsoft’s answer to securely managing local admin credentials during Automated Device Enrollment (ADE). It allows you to provision a local admin account with a randomized, encrypted password that’s stored in Intune and rotated automatically every 6 months.
And yes—it’s finally native. No more weird scripts or third-party tools. Just a few clicks in the ADE profile and you’re good to go.
💡 Key Features
- Randomized Admin Passwords: 15-character strong passwords with upper/lowercase, numbers, and symbols.
- Secure Storage: Passwords are encrypted and stored in Intune.
- Auto-Rotation: Every 6 months, or manually via remote action.
- RBAC Controlled Access: Only custom Intune roles with specific permissions can view or rotate passwords.
- Standard User Support: You can also provision a local standard user account alongside the admin.
In short: this is not just a feature. It’s a requirement in 2025.
🚀 Real-World Setup Notes
We’ve already rolled this out in a few environments, and here’s what stood out:
- ADE is mandatory: LAPS only works during automated device enrollment. If a device is already enrolled, you’ll need to wipe and re-enroll with a LAPS-enabled profile.
- RBAC gotcha: The permissions to view or rotate passwords aren’t included in any built-in roles. You’ll need to create a custom role with
View macOS admin passwordandRotate macOS admin passwordenabled. - macOS 12+ only: Devices must be running macOS Monterey or later.
💬 Lessons from the Field
In our internal testing and customer rollouts, we’ve seen a few things worth noting:
- Zscaler and other proxies can interfere with enrollment and password sync. Make sure the required Intune endpoints are whitelisted.
- Scripted workarounds are finally obsolete. We used to rely on custom scripts to create local admin users and rotate passwords. With LAPS, that’s no longer necessary—and that’s a huge win for security and simplicity.
- ADE profiles need to be updated. If you’re using older profiles, make sure to add the new LAPS settings before deploying.
🛠️ How To Configure it with Intune
1. Create or Edit an ADE Enrollment Profile
- Go to Microsoft Intune Admin Center → Devices → macOS → Enrollment → Enrollment Program Tokens.
- Select your token and choose Profiles.
- Either create a new profile or edit an existing one.
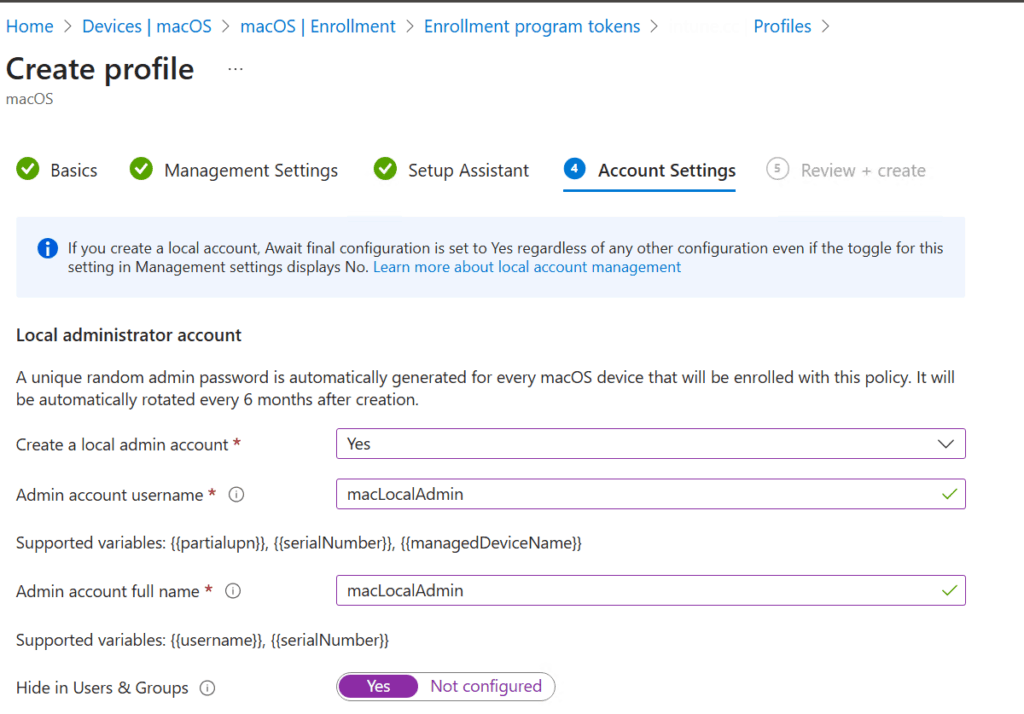
2. Enable LAPS
- In the profile settings, scroll to the “Create a local admin account” section.
- Set “Create a local admin account” to Yes.
- Enable “Rotate password” to Yes.
- Optionally, enable “Create a standard user account” if needed.
3. Assign the Profile
- Assign the profile to your targeted device group.
- Make sure the devices are new or wiped and will go through Automated Device Enrollment (ADE).
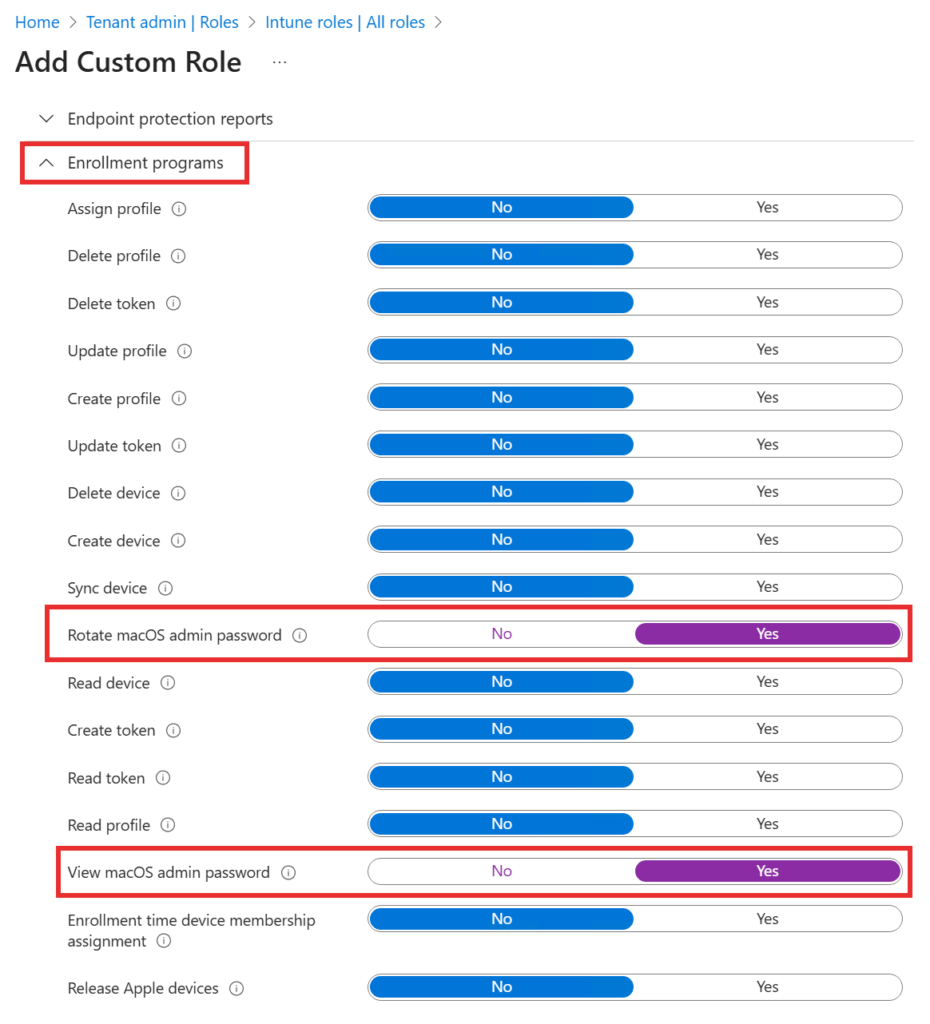
4. Create a Custom Intune Role (RBAC)
- Go to Tenant Administration → Roles → All Roles → + Create.
- Name your role (e.g., “macOS LAPS Admin”).
- Under Permissions, add:
View macOS local admin passwordRotate macOS local admin password
- Assign this role to the appropriate admin group.
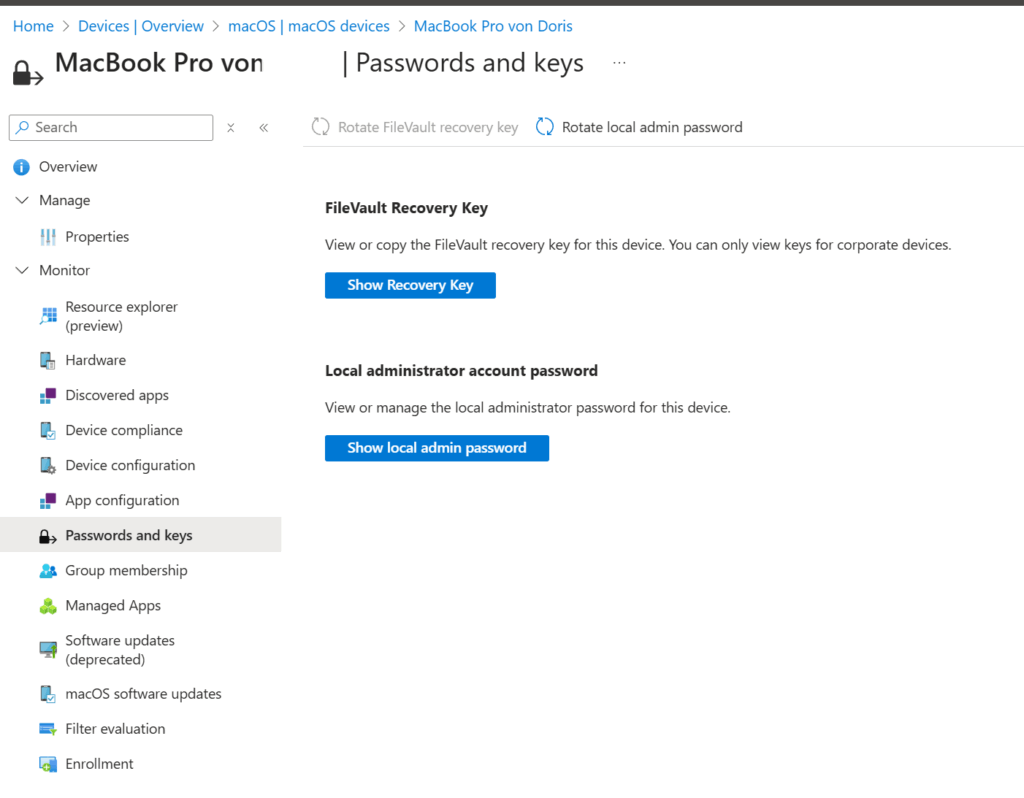
5. Verify Deployment
- After enrollment, go to Devices → macOS → select a device.
- Under Local admin password, you should see the current password and the option to rotate it.
✅ Final Thoughts
macOS LAPS in Intune is one of those features that just makes sense. It’s clean, secure, and finally brings macOS closer to the management experience we’ve had on Windows for years. If you’re managing Apple devices in a corporate environment, this is a no-brainer.

Leave a Reply