🧠 Why ESS & MFU Matter
🔒 ESS isolates biometric data (fingerprint, facial recognition) at the hardware level. This protects against replay and extraction attacks—your face and fingerprint stay yours.
🧩 MFU enforces true two-factor authentication directly on the device. Think PIN + fingerprint or PIN + facial recognition. No cloud dependency, no shortcuts.
Together, they raise the bar for attackers. To break in, they’d need the device, the PIN, and your biometric data. Good luck with that.
⚙️ Quick Tips for Deployment
✅ Enable ESS if hardware supports it
✅ Use MFU to enforce MFA directly on the device
✅ Start with a pilot group
✅ Manage centrally via Intune
✅ Hide password sign-in—but keep it available for emergencies
🛠️ How to Enable ESS & MFU
1️⃣ Check Requirements
- Windows 11
- TPM 2.0
- ESS-capable hardware (internal camera or fingerprint sensor)
- BIOS setting enabled (e.g., “Enhanced Windows Biometric Security”)
⚠️ External devices are not supported!
2️⃣ Test Compatibility
Use PowerShell:WH4B_ESS_Check_Capability_DetectionScript.ps1
<#
Script: WH4B ESS Capability Detection
Author: Daniel Fraubaum
Version: 1.0
Description: Intune Remediation Detection Script. Checks if the device is WH4B ESS-capable by verifying
USB host controllers and cameras for the required capability flag.
#>
####################################################################
# Preferences
####################################################################
$ErrorActionPreference = "SilentlyContinue"
####################################################################
# Variables
####################################################################
$wh4bEssCapableDevices = @()
####################################################################
# Function: Check-WH4BESSCapability
# Description: Checks if a given device has the WH4B ESS capability flag set.
####################################################################
function Check-WH4BESSCapability {
param (
[string]$deviceName
)
$device = Get-PnpDevice | Where-Object { $_.FriendlyName -like "*$deviceName*" }
if ($device) {
$deviceId = $device.InstanceId
$deviceProperties = Get-PnpDeviceProperty -InstanceId $deviceId -KeyName "DEVPKEY_Device_Capabilities"
if ($deviceProperties.Data -band 0x0400) {
Write-Output "The device '$deviceName' is WH4B ESS-capable."
$wh4bEssCapableDevices += $deviceName
}
else {
Write-Output "The device '$deviceName' is not WH4B ESS-capable."
}
}
else {
Write-Output "Device '$deviceName' not found."
}
}
####################################################################
# Check USB Host Controllers
####################################################################
$hostControllers = Get-PnpDevice | Where-Object { $_.FriendlyName -like "*eXtensible Host Controller*" }
foreach ($controller in $hostControllers) {
Check-WH4BESSCapability -deviceName $controller.FriendlyName
}
####################################################################
# Check Cameras
####################################################################
$cameras = Get-PnpDevice -Class Camera -PresentOnly
foreach ($camera in $cameras) {
Check-WH4BESSCapability -deviceName $camera.FriendlyName
}
####################################################################
# Detection Result for Intune
####################################################################
if ($wh4bEssCapableDevices) {
Write-Output "This computer is WH4B ESS-capable."
Exit 0
}
else {
Write-Output "This computer is not WH4B ESS-capable."
Exit 1
}
#end
Run locally or via Intune remediation.
Exclude Windows 365 Cloud PCs via Filter:
(device.deviceModel -notcontains "Cloud PC")3️⃣ Enable ESS in Intune
📍 Intune → Device Configuration → Settings Catalog
Create policy:
Enable ESS with Supported Peripherals → Enabled
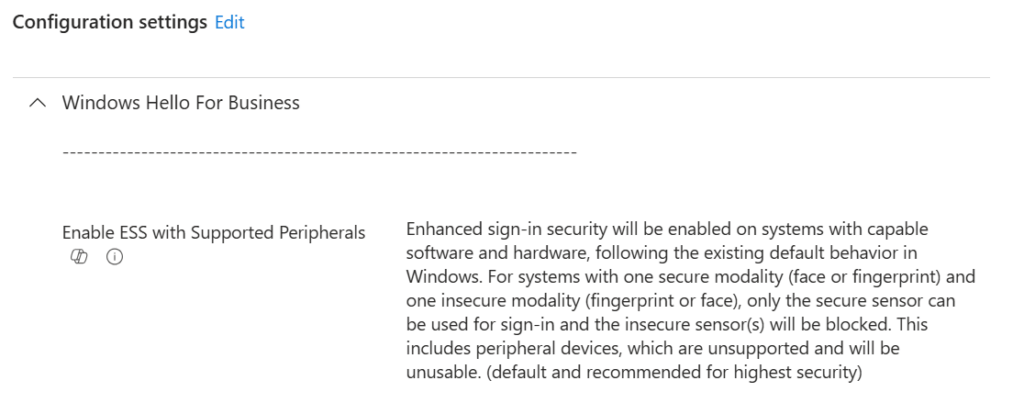
Assign to pilot group, then expand rollout.
4️⃣ Configure MFU with Trusted Signal
To enforce PIN + fingerprint and add a Trusted Signal (like corporate network), use the following setup:
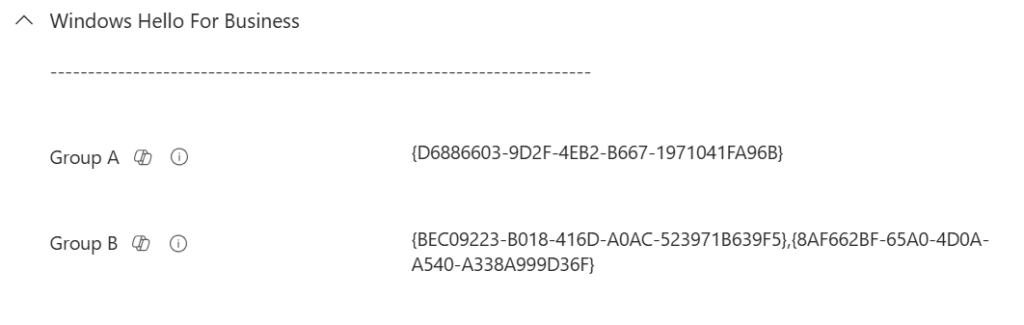
👥 Factor Groups
Group A (First Factor):
- PIN
{D6886603-9D2F-4EB2-B667-1971041FA96B} - Fingerprint
{BEC09223-B018-416D-A0AC-523971B639F5} - Facial Recognition
{8AF662BF-65A0-4D0A-A540-A338A999D36F}
Group B (Second Factor):
- Trusted Signal
{27FBDB57-B613-4AF2-9D7E-4FA7A66C21AD} - PIN
{D6886603-9D2F-4EB2-B667-1971041FA96B} - Fingerprint
{BEC09223-B018-416D-A0AC-523971B639F5} - Facial Recognition
{8AF662BF-65A0-4D0A-A540-A338A999D36F}
🔍 Trusted Signals can include IP address, Bluetooth, WiFi, and more.
5️⃣ Verify ESS Deployment
Use PowerShell:WH4B_ESS_Verify_Enablement_DetectionScript.ps1
<#
Script: WH4B ESS Enabled Verification
Author: Daniel Fraubaum
Version: 1.0
Description: Intune Remediation Detection Script. Verifies if WH4B ESS has been enabled by checking
Windows Biometric Event Logs for specific entries related to internal camera and VSM.
#>
####################################################################
# Variables
####################################################################
$LogPath = "Microsoft-Windows-Biometrics/Operational"
$EventID = 1108
$SearchText1 = "(ROOT\WINDOWSHELLOFACESOFTWAREDRIVER\0000)"
$SearchText2 = "Virtual Secure Mode"
####################################################################
# Check if the log exists
####################################################################
if (Get-WinEvent -ListLog $LogPath -ErrorAction SilentlyContinue) {
Write-Host "Searching for Event ID $EventID in log: $LogPath`n"
# Retrieve events with the specified ID
$Events = Get-WinEvent -LogName $LogPath -FilterXPath "*[System[EventID=$EventID]]"
if ($Events) {
Write-Host "Found the following events:`n"
foreach ($Event in $Events) {
Write-Host "TimeCreated: $($Event.TimeCreated)"
Write-Host "Message: $($Event.Message)"
Write-Host "------------------------------------"
}
}
else {
Write-Host "No events with ID $EventID found in the log: $LogPath"
}
}
else {
Write-Host "The specified log path '$LogPath' does not exist or is not accessible."
}
####################################################################
# Check if event messages contain the required WH4B ESS indicators
####################################################################
$MatchingEvents = $Events | Where-Object { $_.Message -like "*$SearchText1*" -and $_.Message -like "*$SearchText2*" }
if ($MatchingEvents) {
Write-Host "`nEvents containing the text '$SearchText1' and '$SearchText2':`n"
foreach ($Event in $MatchingEvents) {
Write-Host "TimeCreated: $($Event.TimeCreated)"
Write-Host "Message: $($Event.Message)"
Write-Host "------------------------------------"
Write-Output "WH4B ESS has been enabled"
Exit 0
}
}
else {
Write-Host "`nNo events containing the text '$SearchText1' and '$SearchText2' found."
Write-Output "WH4B ESS has not been enabled"
Exit 1
}
#end
Apply as detection script to your test group.
✅ Final Thoughts
ESS and MFU bring enterprise-grade security to Windows endpoints. Biometric data is hardware-protected, and every login requires multiple factors. Even with a stolen device and PIN, attackers face serious friction.
Security that works with users—not against them.


Leave a Reply