In modern environments where devices are joined only to Microsoft Entra ID, enabling seamless access to on-premises resources like file shares or legacy applications can be a challenge. This blog post walks through how to configure Cloud Kerberos Trust to enable Single Sign-On (SSO) for Entra-only joined devices—without requiring a hybrid join or certificate-based trust.
🧰 Prerequisites
- Microsoft Entra ID P1 or P2 license
- Entra Only Joined device
- Windows 10/11 Enterprise or Education
- Domain Controllers running Windows Server 2016 or later
- Microsoft Entra Connect installed
- Intune (for Hello for Business policy deployment)
🖥️ Step 1: Prepare the Entra Connect Server
Run the following on your Entra Connect server to ensure TLS 1.2 is enabled and install the required PowerShell module:
# Ensure TLS 1.2 for PowerShell gallery access
[Net.ServicePointManager]::SecurityProtocol = [Net.ServicePointManager]::SecurityProtocol -bor [Net.SecurityProtocolType]::Tls12
# Install the AzureADHybridAuthenticationManagement PowerShell module
Install-Module -Name AzureADHybridAuthenticationManagement -AllowClobber🛠️ Step 2: Configure the Cloud Kerberos Trust
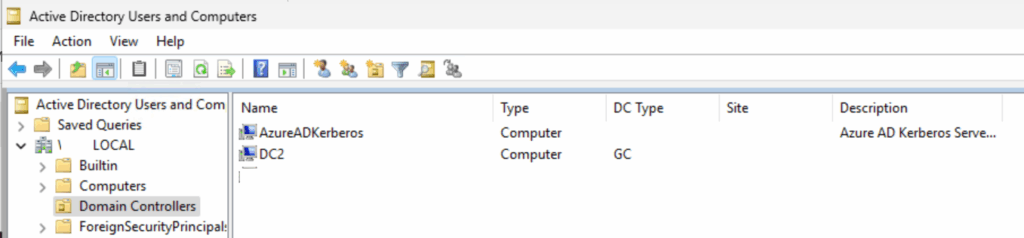
Now configure the Kerberos Server object in your on-prem Active Directory and publish it to Entra ID:
# Define your on-prem domain
$domain = $env:USERDNSDOMAIN
# UPN of a Hybrid Identity Administrator
$userPrincipalName = "administrator@contoso.onmicrosoft.com"
# Domain Admin credentials
$domainCred = Get-Credential
# Create and publish the Kerberos Server object
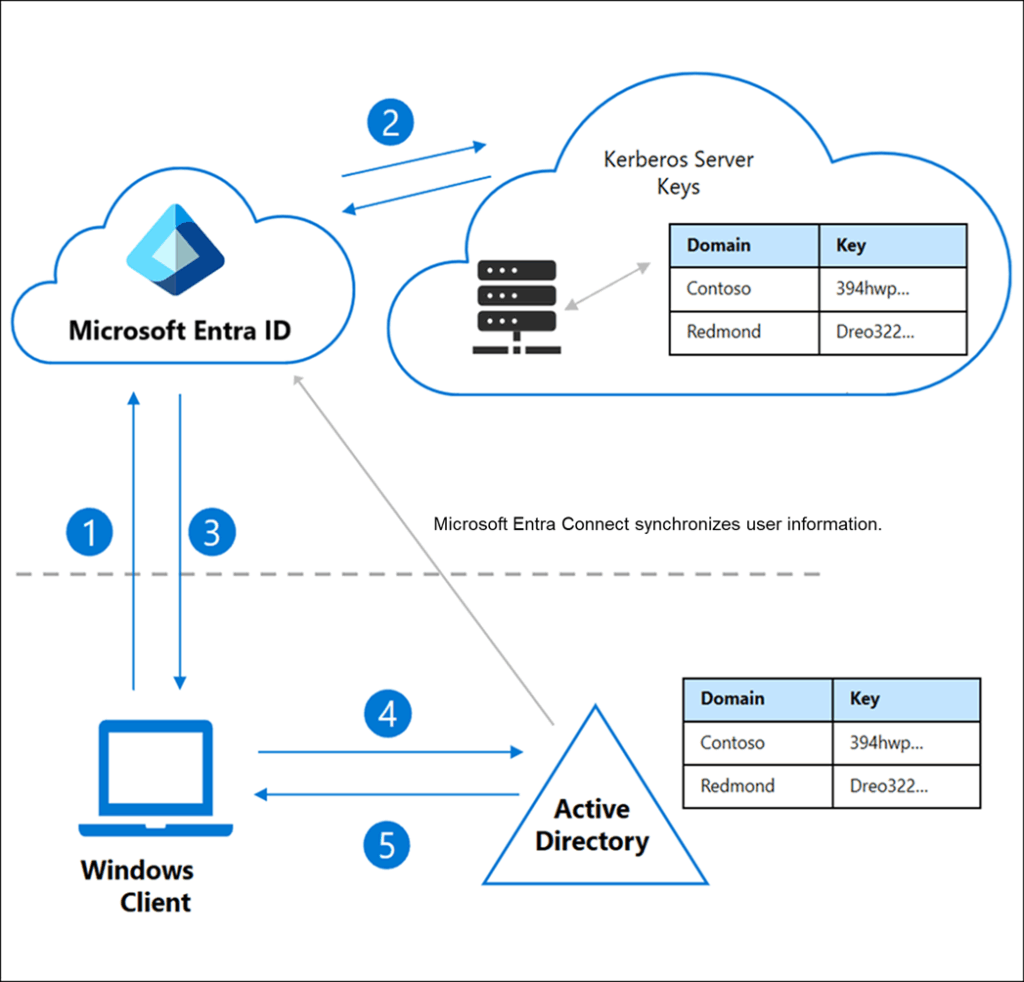
Set-AzureADKerberosServer -Domain $domain -UserPrincipalName $userPrincipalName -DomainCredential $domainCredThis command creates a Kerberos Server object in your on-prem AD and syncs it to Entra ID, enabling Kerberos authentication for Entra-only devices:
📋 Step 3: Deploy the Cloud Trust Policy via Intune
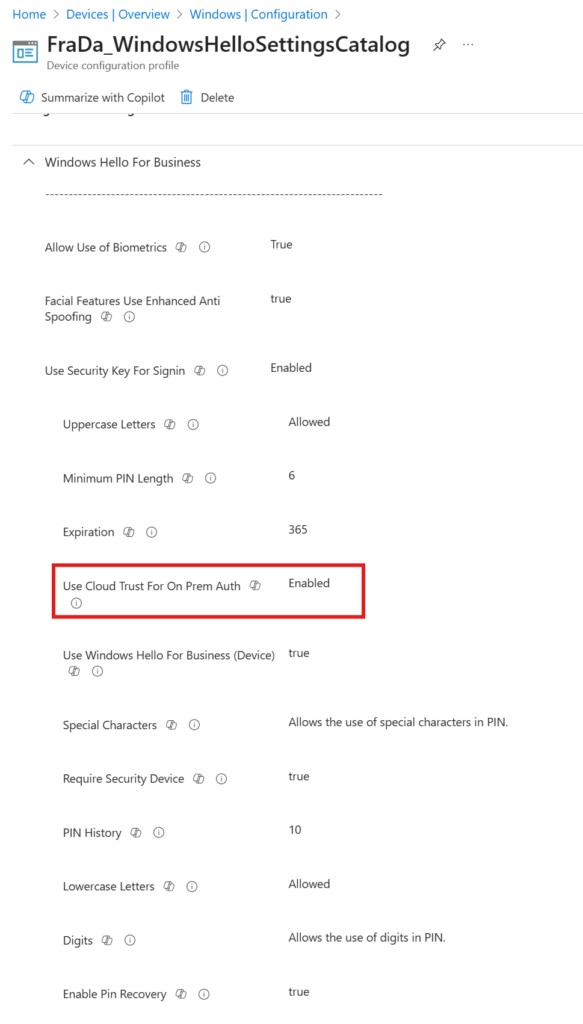
Use the Settings Catalog in Intune to configure the Windows Hello for Business policy:
- Go to Endpoint Manager Admin Center → Devices → Configuration profiles
- Create a new profile:
- Platform: Windows 10 and later
- Profile type: Settings catalog
- Add the following settings:
- Use cloud trust for on-premises authentication → Enabled
- Configure Windows Hello for Business → Enabled
- Use biometrics → Enabled (optional)
- PIN complexity → as per your policy
This ensures that Entra-only devices can use Windows Hello for Business with Cloud Kerberos Trust to authenticate to on-prem resources.
Summary
With Cloud Kerberos Trust, you can:
- Eliminate the need for hybrid join or certificate-based trust
- Enable seamless SSO to on-prem resources
- Simplify your infrastructure and reduce dependency on ADFS or PKI

Leave a Reply