With Windows 11, Microsoft continues to blur the lines between system components and Store apps. Notepad, Calculator, even Paint – they’re all Store apps now. And while that’s great for updates and modularity, it’s a headache for IT admins trying to keep user environments clean and controlled.
For a while, blocking the Microsoft Store via Intune policies was enough. But times have changed.
🧩 The Problem: apps.microsoft.com
Microsoft quietly introduced a new web interface at apps.microsoft.com, allowing users to download Store apps directly from the browser. No admin rights required. The apps install into the user profile, bypassing traditional controls like UAC prompts or installation policies.
This means even with the Store blocked via Intune, users can still grab apps like Spotify, WhatsApp, or worse – random developer tools – straight from the browser.
🛑 The Classic Block: Intune Store Policy
Before diving into browser-specific controls, let’s recap the standard method:
In Intune, you can configure a Device Configuration Profile using Administrative Templates to block the Store app:
- Policy Name: Turn off the Store application
- Path:
SettingsCatalog > Administrative Templates > Windows Components > Store - Settingname: Turn off the Store application
- Setting: Enabled
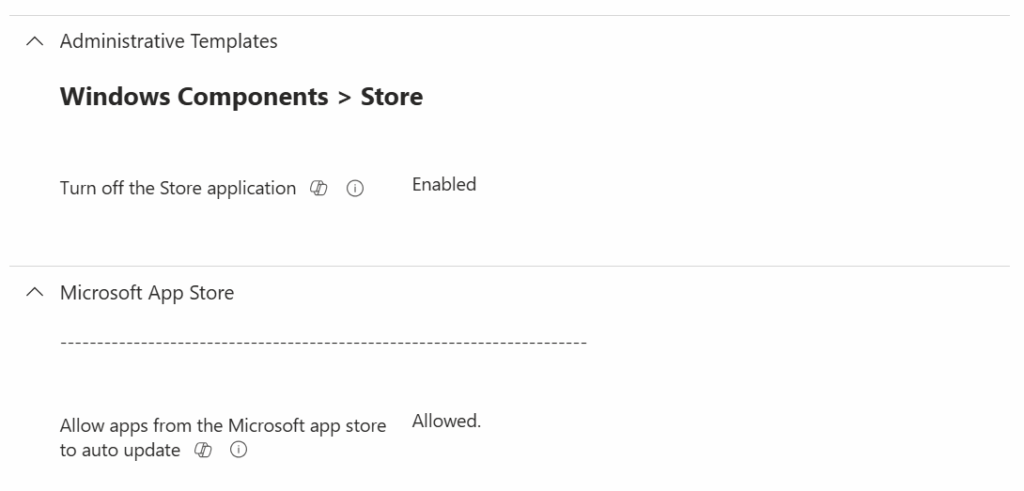
This disables the Store app itself – but does not block access to apps.microsoft.com. That’s why additional browser-level controls are now essential.
🧠 The Smart Block: Browser-Level URL Filtering
The simplest and most effective method is to block the URL only in the browser. This way, users can’t access the site to download new apps, but Store updates continue to work in the background.
Here’s how to do it:
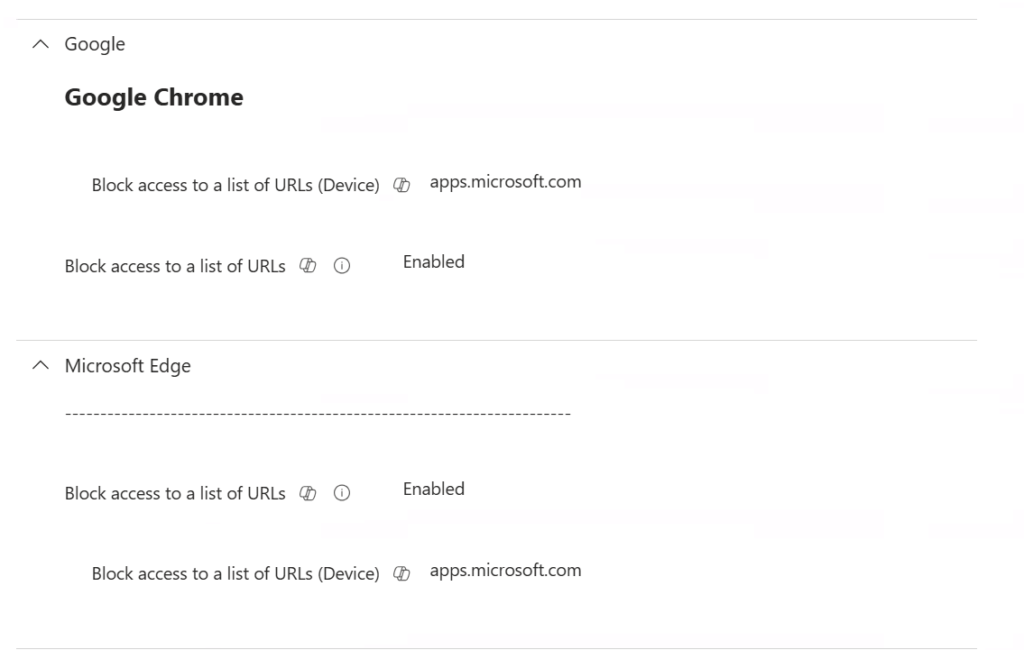
🔧 Microsoft Edge
Use Intune to deploy a SettingsCatalog Policy:
- Policy Name: URL Block List
- Path:
SettingsCatalog > Microsoft Edge - Setting: Block access to a list of URLs
- Value:
apps.microsoft.com
This will prevent users from accessing the site in Edge.
🌐 Google Chrome
Chrome also supports SettingsCatalog in Intune.
- Policy Name: URL Block List Chrome
- Path:
SettingsCatalog > Google Chrome - Setting: Block access to a list of URLs
- Value:
apps.microsoft.com
🦊 Mozilla Firefox
Firefox supports ADMX templates as well. You can block websites natively using the WebsiteFilter policy:
- Policy Name: WebsiteFilter
- Setting: Block websites from being visited
- Value:
apps.microsoft.com
This can be deployed via Intune using the Firefox ADMX templates. No need for extensions or workarounds – it’s clean and native.
🧪 What About WDAC or AppLocker?
Solutions like Windows Defender Application Control (WDAC) or AppLocker offer deep control over what runs on endpoints. In larger enterprises, these are highly recommended and often part of a broader security strategy.
However, for smaller organizations or environments without dedicated security teams, these tools can be complex to implement and maintain. For this specific use case – blocking a single site – browser-level filtering is a lightweight and effective alternative.
✅ Summary
- Problem: Users can install Store apps via apps.microsoft.com without admin rights.
- Classic block: Intune Store policy disables the app, but not the website.
- Firewall block: Not viable – breaks Store updates.
- Best solution: Block the site in browsers via Intune policies.
- Enterprise options: WDAC/AppLocker are powerful but may be overkill for smaller setups.
This trick keeps your environment clean without breaking essential functionality. And it’s easy to roll out across your fleet.


Leave a Reply